Legacy firewalls have long been the backbone of network security for many organisations. However, with the rise of cloud computing and virtualisation, many organisations are moving away from traditional legacy firewalls in favour of software-defined networking solutions like VMware NSX. In this article, we will explore how to clone legacy firewall rules and implement them in VMware NSX.
Step 1: Document Legacy Firewall Rules.
The first step in cloning legacy firewall rules is to document them. This includes not only the rules themselves, but also the associated policies and procedures. This documentation will be critical in ensuring that the cloned rules are configured correctly in VMware NSX.
Step 2: Map Legacy Firewall Rules to NSX Policies.
Once the legacy firewall rules have been documented, the next step is to map them to VMware NSX policies. This involves identifying the policies in VMware NSX that are equivalent to the legacy firewall rules. For example, if a legacy firewall rule allows traffic from a specific IP address to a specific port, the equivalent policy in VMware NSX would be a firewall rule that allows traffic from a security group to a specific port.
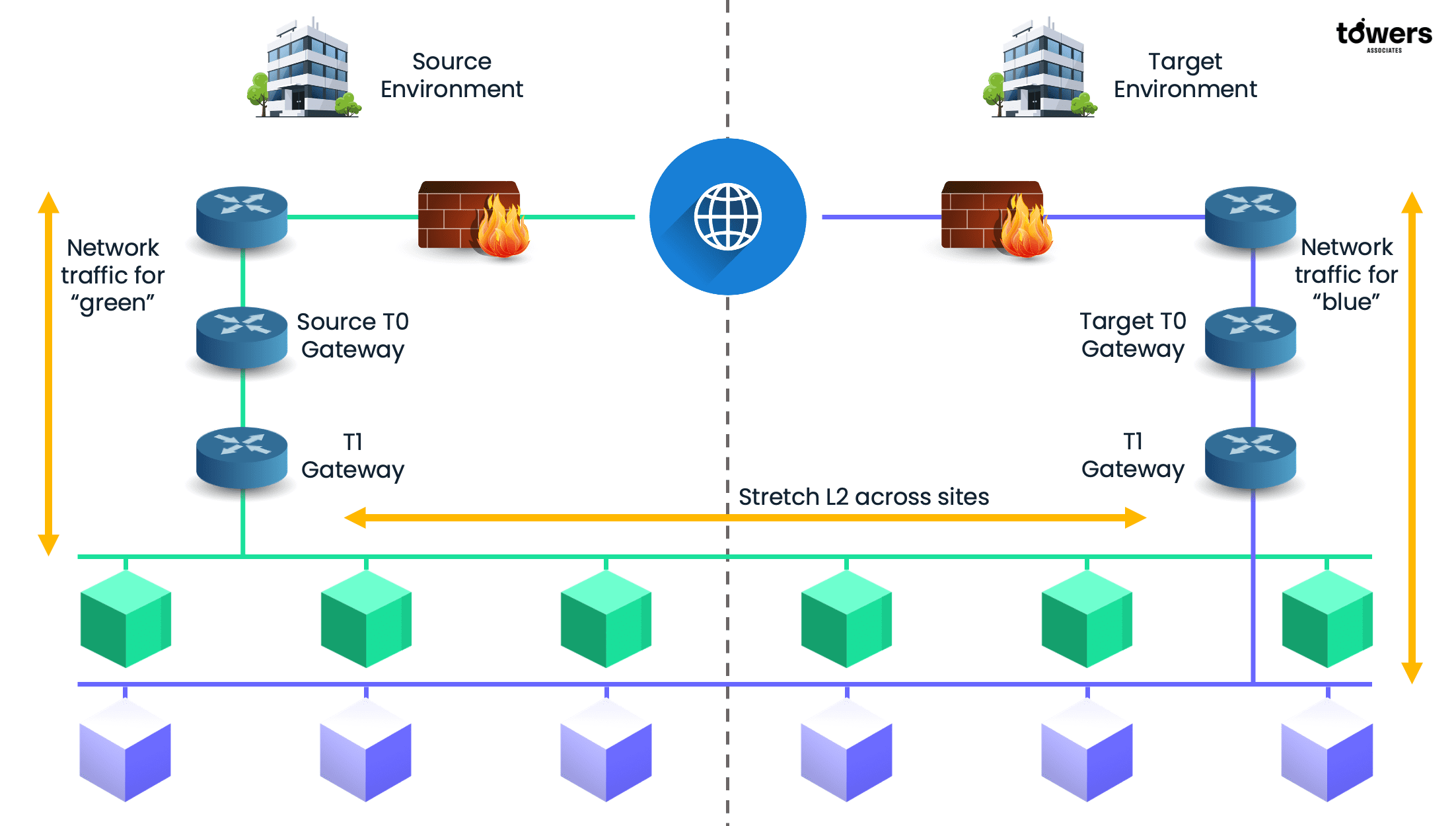
Below is a diagram that represents the process:
Step 3: Create Security Groups in VMware NSX.
In VMware NSX, security groups are used to group virtual machines and apply policies to them. To clone legacy firewall rules, it is necessary to create security groups in VMware NSX that correspond to the groups of virtual machines that were protected by the legacy firewall rules. This may require some reconfiguration of virtual machines to ensure that they are correctly grouped.
Step 4: Create Firewall Rules in VMware NSX.
Once the security groups have been created, the next step is to create firewall rules in VMware NSX that correspond to the legacy firewall rules. This involves specifying the source and destination IP addresses, ports, and protocols for each rule. It is important to ensure that the rules are configured correctly to provide the necessary level of protection for the virtual machines.
Step 5: Test and Validate Firewall Rules.
After the firewall rules have been created, it is important to test and validate them. This involves verifying that the rules are correctly configured and that they provide the intended level of protection for the virtual machines. This may require some fine-tuning of the rules to ensure that they are working correctly.
In conclusion, cloning legacy firewall rules and implementing them in VMware NSX requires a systematic approach that involves documenting the legacy firewall rules, mapping them to VMware NSX policies, creating security groups in VMware NSX, creating firewall rules in VMware NSX, and testing and validating the rules. By following these steps, we’ve successfully supported organisations in migrating from legacy firewalls to VMware NSX, and done so with confidence, knowing that their virtual machines are protected by policies that are equivalent to their legacy firewall rules.
Contact us to find out more.